A Hidden Threat: How Mesh Detects QR Code Phishing “Quishing” Video Breakdown.
Introduction
In recent months, there has been a significant rise in QR code phishing attacks, successfully bypassing email filters and leading to compromised mailboxes. Why are QR code, also known as “Quishing,” attacks becoming more popular?
These appear harmless as we use QR codes from restaurant menus to airline tickets. However, they are an effective way to hide a malicious threat. The QR code itself can conceal a malicious link, which can appear as a standard image if not actively scanned and parsed.
Given the widespread use of scanning QR codes daily by millions of people, receiving one in an email won't be perceived as an immediate cause for concern. As we analyze, we'll show real examples to improve understanding and awareness, crucial given the rising complexity of QR code phishing attacks.
In this blog, we will present:
Illustrative Examples: Real-life instances of “Quishing”, providing examples for better understanding and awareness.
Insights for Vigilance: Gain valuable insights into what to watch out for, especially as we approach the holiday season.
Mesh’s Detection Engine: Explore how Mesh's detection engine scans for any malicious URLs hidden within QR Codes.
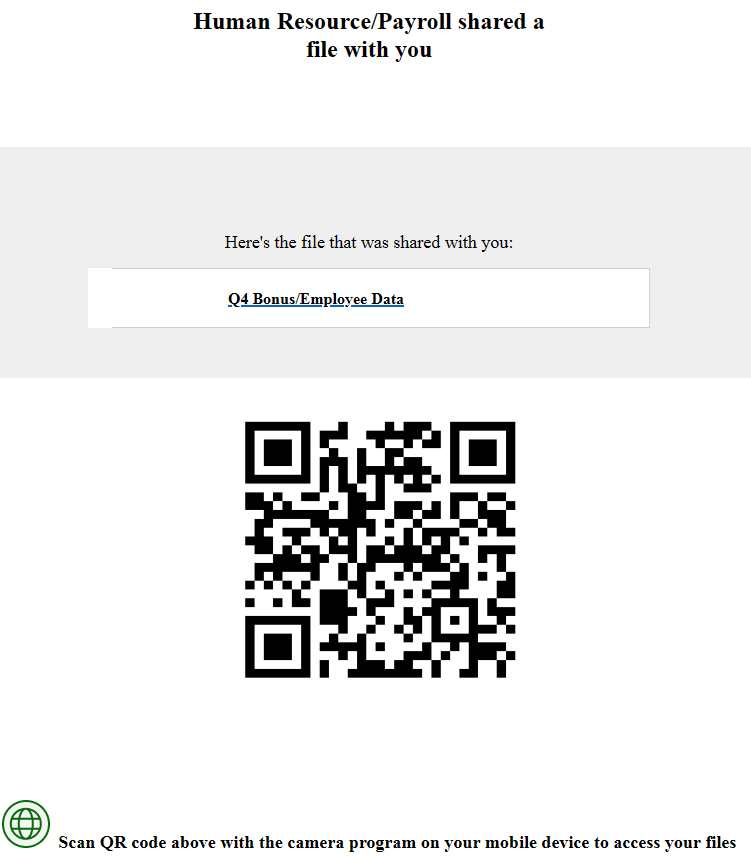
Example 1:
Q4 Bonus Anticipation: The subject line tempts the recipient with the promise of a Q4 bonus—something employees may be expecting this time of year, or it could be a welcome surprise.
Engaging Call to Action: The Call to Action invites the recipient to engage through a shared "file" and a QR code to access the Q4 bonus information.
Example 2:
Enhanced Content: The email content not only focuses on text but also features the company logo it aims to imitate. Additionally, it references a widely used accounting software, Sage.
Personalized Elements: Multiple times throughout the email, it addresses the recipient by name and makes references to their specific company.
Example 3:
Impersonation through Display Name: The display name mimics HR or the Accounting Department, similar to previous examples.
Urgency: The message creates urgency with the plea, "Please sign at your earliest convenience," a common tactic to pressure individuals.
Mimicking DocuSign: The email imitates the appearance of a DocuSign email.
Conclusion
Our image analyzer can detect QR codes in emails, parsing and decoding them to scan for potentially malicious hidden URLs.
With email security threats evolving rapidly, it is crucial for MSPs to partner with security providers that stay ahead of new and emerging attacks.
Mesh not only detects and blocks Quishing attacks, but secures both the email perimeter and mailbox in a single solution - Mesh Unified.
Start your free trial / get your NFR account today - https://www.meshsecurity.io/free-trial